 Account Takeover Attacks (ATOs) have become a pressing concern in today’s digital landscape. These malicious activities involve unauthorized individuals gaining control over user accounts, resulting in a multitude of potential consequences. From accessing personal information to inflicting financial loss and reputational damage, the implications of ATOs are far-reaching and require immediate attention.
Account Takeover Attacks (ATOs) have become a pressing concern in today’s digital landscape. These malicious activities involve unauthorized individuals gaining control over user accounts, resulting in a multitude of potential consequences. From accessing personal information to inflicting financial loss and reputational damage, the implications of ATOs are far-reaching and require immediate attention.
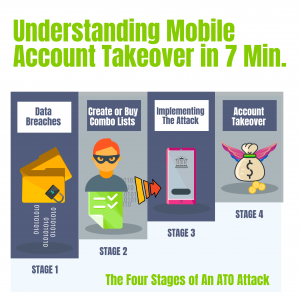
ATOs refer to the unauthorized acquisition and misuse of online accounts, typically achieved through various methods such as phishing, brute-force attacks, or exploiting weak passwords. With the growing reliance on digital platforms for various activities, including banking, shopping, and social media interaction, the significance of ATOs cannot be understated.
One of the most alarming consequences of ATOs is the unauthorized access to personal information. Once a hacker gains control of an account, they can extract sensitive data such as social security numbers, addresses, and contact information. This information can then be used for identity theft or sold on the black market, exposing victims to financial and personal turmoil.
Financial loss is another severe consequence of ATOs. Attackers can exploit compromised accounts to make unauthorized transactions, transfer funds, or even open new lines of credit in the victim’s name. This can lead to extensive financial hardships for individuals and businesses alike, with the potential for long-term repercussions on their financial stability.
Moreover, ATOs can cause significant reputational damage to both individuals and organizations. Hackers can use compromised accounts to distribute malicious content, spam messages, or engage in fraudulent activities, all under the victim’s name. This can tarnish one’s online reputation, leading to mistrust among peers, colleagues, and even potential employers. For businesses, such attacks can result in customer loss, negative publicity, and a damaged brand image that is difficult to recover from.
The consequences of ATOs are not limited to individuals or businesses alone; they also pose a significant threat to the overall digital ecosystem. These attacks undermine user confidence and trust in online platforms, hindering the growth and adoption of digital services. Furthermore, the financial burden associated with preventing, mitigating, and recovering from ATOs puts a strain on organizations, diverting resources that could be better utilized for innovation and development.
To combat the increasing prevalence of ATOs, individuals and organizations must prioritize their cybersecurity measures. Employing strong, unique passwords, enabling two-factor authentication, and staying vigilant against phishing attempts are essential steps in safeguarding against ATOs. Additionally, organizations should invest in robust security systems, educate their users about potential threats, and regularly monitor and detect suspicious activities.
In conclusion, the significance of Account Takeover Attacks (ATOs) in today’s digital landscape cannot be ignored. The potential consequences, including unauthorized access to personal information, financial loss, and reputational damage, highlight the urgent need for proactive cybersecurity measures. By prioritizing security practices and remaining vigilant, individuals and organizations can mitigate the risks associated with ATOs, fostering a safer digital environment for all.
Common Techniques Used in ATOs
Attackers are constantly evolving their methods to infiltrate online accounts, gaining unauthorized access and causing potential harm. In this article, we will explore the various techniques employed by attackers to carry out Account Takeover (ATO) incidents, shedding light on the importance of robust security measures for individuals and organizations alike.
Phishing is one of the most prevalent techniques used in ATOs. Attackers employ deceptive emails, messages, or websites to trick individuals into revealing their login credentials. These phishing attempts often pose as legitimate sources, such as financial institutions or online services, creating a sense of urgency or fear to manipulate users into divulging their sensitive information. Vigilance and skepticism when encountering suspicious emails or URLs are vital to preventing falling victim to these attacks.
Another common method utilized in ATO incidents is social engineering. Attackers exploit psychological manipulation to deceive individuals into divulging their login credentials or personal information. This can be achieved through impersonation, where attackers pose as trustworthy individuals or organizations to gain the victim’s trust and extract sensitive details. Awareness and education regarding social engineering tactics are crucial to avoid becoming a victim of such attacks.
Brute-force attacks are a more direct approach employed by attackers. This technique involves systematically attempting various combinations of usernames and passwords until the correct credentials are discovered. Attackers often leverage automated tools to accelerate the process, making it imperative for users to employ strong, unique passwords and enable multi-factor authentication to mitigate the risk of successful brute-force attacks.
Credential stuffing is another technique frequently utilized in ATO incidents. Attackers leverage previously leaked username and password combinations from other data breaches to gain unauthorized access to other accounts where individuals reused their credentials. This highlights the importance of using unique passwords for each online account to minimize the impact of credential stuffing attacks.
Exploiting weak passwords or security vulnerabilities is yet another avenue attackers explore in ATO incidents. Individuals often opt for easily guessable passwords or fail to update their credentials regularly, unknowingly leaving themselves vulnerable to unauthorized access. Additionally, software or system vulnerabilities that have not been patched provide opportunities for attackers to exploit and gain access to accounts. Regularly updating passwords and promptly patching software vulnerabilities are essential preventive measures to impede attackers from exploiting these weaknesses.
In conclusion, understanding the common techniques deployed by attackers in Account Takeover incidents is essential for individuals and organizations to strengthen their security measures. By being cautious of phishing attempts, aware of social engineering tactics, employing strong passwords, utilizing multi-factor authentication, and promptly patching vulnerabilities, individuals can significantly reduce the risk of falling victim to ATO incidents. Additionally, organizations should prioritize educating their employees and implementing robust security practices to safeguard customer accounts and maintain their trust. Together, we can fortify our online defenses and protect ourselves from the ever-evolving threat landscape.
Recognizing and Preventing ATOs:
In today’s digital age, the threat of account takeover (ATO) attempts is more prevalent than ever before. Cybercriminals are constantly devising new strategies to gain unauthorized access to personal and sensitive information, putting individuals and businesses at risk. It is crucial for internet users to be aware of these potential threats and take proactive measures to prevent falling victim to ATO attacks.
One of the first steps to safeguarding your online accounts is to create strong and unique passwords. Many individuals make the mistake of using easily guessable passwords or reusing the same password across multiple accounts, making it easier for hackers to gain access. It is recommended to use a combination of upper and lowercase letters, numbers, and symbols when creating passwords. Furthermore, regularly updating passwords can add an extra layer of security.
In addition to strong passwords, utilizing multi-factor authentication (MFA) can significantly enhance the security of your accounts. MFA provides an extra verification step, usually through a code sent to your mobile device, ensuring that even if your password is compromised, hackers cannot gain access without the secondary authentication factor. Enabling MFA whenever available is a simple yet effective way to prevent unauthorized access to your accounts.
Monitoring account activity is another crucial practice to prevent ATOs. By regularly reviewing your account statements and notifications, you can quickly identify any suspicious activity or unauthorized access attempts. If there are any discrepancies or activities you do not recognize, it is important to report them immediately to your service provider or financial institution. Timely action can help mitigate potential damages and prevent further unauthorized access.
However, it is not only about securing your accounts internally. It is equally important to exercise caution when dealing with suspicious emails, links, or requests for personal information. Phishing attacks have become increasingly sophisticated, often mimicking legitimate organizations or individuals to deceive unsuspecting victims. Always be skeptical of emails or messages requesting personal information and avoid clicking on suspicious links. It is advisable to verify the authenticity of such requests independently, either by contacting the organization directly or through a trusted source.
In conclusion, preventing ATOs requires a combination of proactive measures and vigilant behavior. By implementing strong and unique passwords, utilizing multi-factor authentication, regularly monitoring account activity, and being cautious with suspicious emails or requests, individuals can significantly reduce the risk of falling victim to ATO attacks. Remember, staying informed and proactive is key to protecting your personal and sensitive information in the digital world we live in today.
Strengthening Security Measures:
In today’s digital age, it has become more important than ever to prioritize our online security. With the rise in Account Takeover (ATO) attacks, it is crucial for individuals and businesses to enhance their security measures to protect sensitive information. Luckily, there are practical tips that can greatly reduce the risk of falling victim to these malicious attacks.
One effective way to bolster security is by utilizing password managers. These tools not only generate complex and unique passwords for each of your accounts, but they also securely store them, eliminating the need to remember numerous complex passwords. By using a reputable password manager, such as LastPass or Dashlane, you can ensure that your login credentials are not easily compromised. Remember, the stronger and more unique your passwords are, the harder it is for hackers to crack them.
Additionally, implementing Multi-Factor Authentication (MFA) adds an extra layer of protection to your accounts. MFA requires you to provide multiple forms of verification, such as a password and a one-time code sent to your mobile device, before gaining access. This significantly reduces the chances of unauthorized individuals gaining control of your accounts, even if they manage to obtain your password. Whenever possible, enable MFA on your online accounts, especially for sensitive information like banking or email.
While password managers and MFA are effective measures, it is crucial to regularly conduct security audits. These audits involve assessing your security systems, identifying any vulnerabilities, and taking steps to address them promptly. By conducting periodic security audits, you can stay one step ahead of potential attackers and ensure your systems are up-to-date with the latest security patches and measures.
Remember, the world of cybersecurity is constantly evolving, and attackers are becoming more sophisticated in their techniques. Therefore, it is essential to stay informed about the latest security practices and trends. Many security experts and organizations regularly publish reports and articles on emerging threats and best practices, which can help you stay ahead of potential risks.
In conclusion, by following practical tips to enhance security measures, you can substantially reduce the risk of falling victim to Account Takeover attacks. Utilizing password managers, enabling Multi-Factor Authentication, and conducting regular security audits are all effective ways to protect your personal and business information. By staying proactive and informed about the latest security practices, you can ensure that your online presence remains secure in an increasingly digital world.